Cloud-native protection
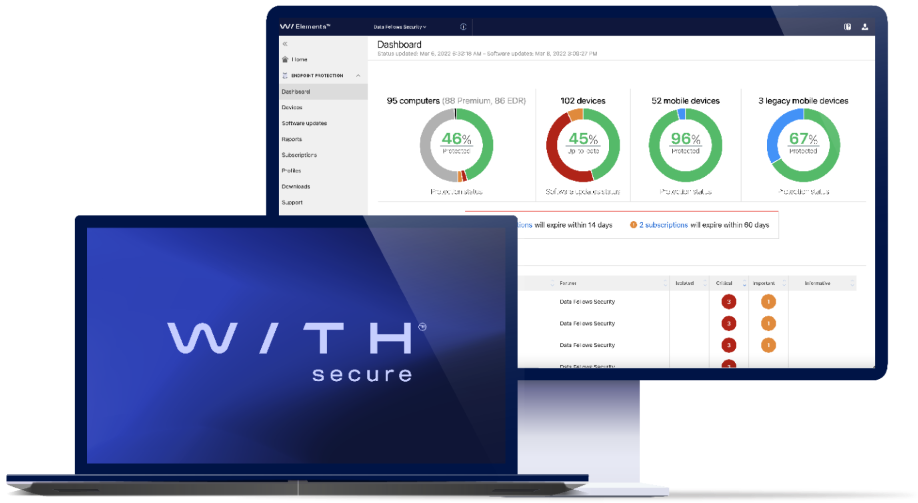
WithSecure™ Elements Endpoint Protection (EPP) is designed to protect endpoints on all your devices, from computers and servers to mobiles. The cloud-native solution saves you time in deploying, managing and monitoring security. It works by keeping your organization safe from even the most advanced threats, exploits, and fileless attacks – including malware and ransomware.
Our solution has everything your business needs for endpoint protection, including fully integrated patch management capabilities, layered protection, and advanced behavior and empirical analysis. It provides maximum security with minimum maintenance and management overhead, beating competing products and regularly scoring highly for best protection in the industry.