F-Secure Elements Vulnerability Management
Harden your attack surface
Vulnerability scanning and insights managed for you by File Sanctuary
Scan and manage vulnerabilities in your network
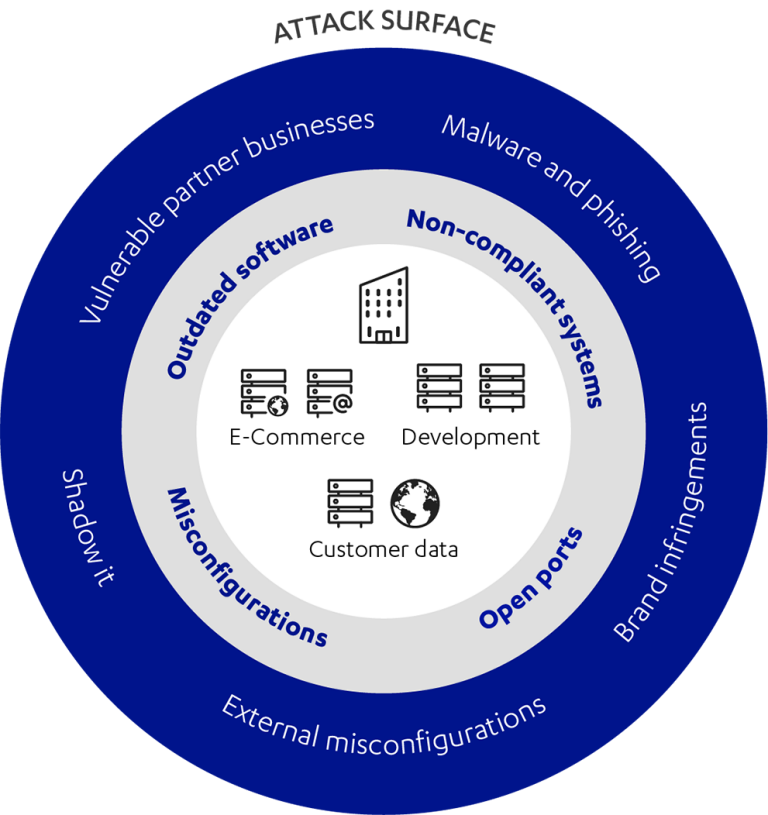
Attackers only need one way in – don’t let them have it.
Get a risk-based view of your whole attack surface – from your network to software to web apps – so you can find, prioritise and fix known, unknown and potential vulnerabilities before they’re exploited.
Vulnerability Management is an easy-to-deploy, cloud-based vulnerability scanner that covers your network, assets, the deep web and compliance. And it automatically reports activities like brand violations, third-party scams and phishing sites. Manage F-Secure Elements Vulnerability Management in the cloud or use as a fully-outsourced managed service from one of our certified partners.
F-Secure Elements Vulnerability Management is part of F-Secure Elements, the one platform that delivers everything from vulnerability management and collaboration protection to endpoint protection; and detection and response – managed from a single security console. Use individual solutions for specific needs or get complete protection by combining them all.
Why F-Secure Elements Vulnerability Management?

Scan the deep web

Fight brand exploit

Cut costs
A powerful solution
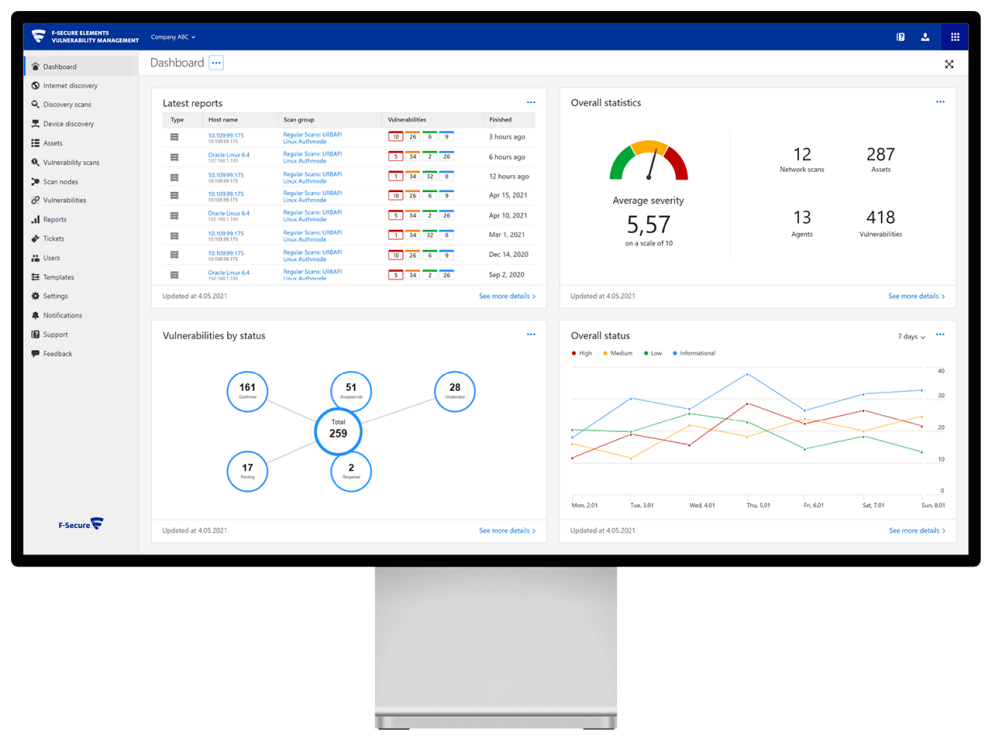
- Vulnerability Management dashboard is a single console monitoring the current status of vulnerabilities and incidents
- Vulnerability Management endpoint agent is a Windows application that automatically collects data from all your endpoints
- Internet asset discovery crawls the Internet (including deep web) to find your organization’s Internet-facing systems
- Discovery scans lets you discover all hosts and network devices in your infrastructure
- Vulnerability scans scan systems for any known vulnerabilities like ransomware or other malicious software
- Vulnerability management centrally through a single console with automated detection and reporting
- PCI DSS compliance requirements are met by F-Secure Elements Vulnerability Management, reducing the risk of data loss
